Long story short: During the transition of antivirus software to Windows Defender Antivirus (WinDefend), I don't want Windows Defender remediation on threats it might find. Later, when I have more information about potential threats, I can always choose to remediate that threat, e.g. quarantaine or remove it. Unfortunately, there is no PowerShell cmdlet to configure this. Here is how to (temporarily) turn off routine remediation.
Configure Microsoft Defender Antivirus with Group Policy. You can turn off Windows Defender routine remediation using a GPO setting called "DisableRoutinelyTakingAction". This policy setting allows you to configure whether Microsoft Defender Antivirus automatically takes action on all detected threats. Enable this and you're all set.
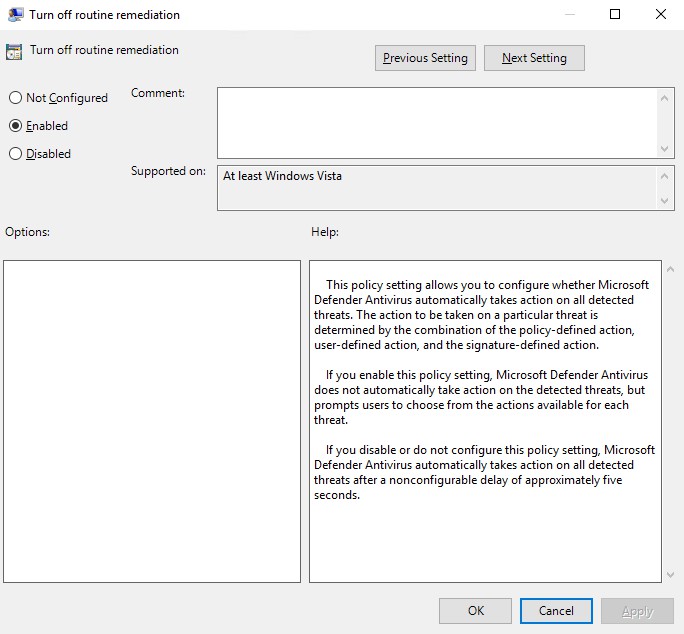
If you enable this policy setting, Windows Defender does not
automatically take action on the detected threats, but prompts
users to choose from the actions available for each threat.
If you are in an environment where there is no Group Policy, you can always configure DisableRoutinelyTakingAction in the Windows registry:
Set-ItemProperty `
-Path "HKLM:\Software\Policies\Microsoft\Windows Defender" `
-Name "DisableRoutinelyTakingAction" `
-Value 1 `
-Type DWORD
How-to fix "Get-MpComputerStatus : The extrinsic Method could not be executed."
You can configure some default actions using Set-MpPreference. However, there is a lot of uncertainty about different ThreatDefaultAction settings for Windows Defender Antivirus (HighThreatDefaultAction, LowThreatDefaultAction, ModerateThreatDefaultAction, SevereThreatDefaultAction, UnknownThreatDefaultAction).
Two remediation values you can set are: 6 and 9:
| Value | Action | |
|---|---|---|
| 1 | Clean the detected threat. | |
| 2 | Quarantine the detected threat. | |
| 3 | Remove the detected threat. | |
| 6 | Allow the detected threat. | |
| 8 | Allow the user to determine the action to take with the detected threat. | |
| 9 | Do not take any action. | |
| 10 | Block the detected threat. | |
| 0 | (NULL) | Apply action based on the Security Intelligence Update (SIU). This is the default value. |
You might think both are what I want, but no. Setting *ThreatDefaultAction to 6 makes Windows Defender Antivirus completely ignore the threat and doesn't report it the Eventlog (or Get-MpThreat). Setting the actions to 9 causes Windows Defender to actively act on the threats and generates event id 1117 (MALWAREPROTECTION_STATE_MALWARE_ACTION_TAKEN).
Therefore, configuring and turning this routine remediation off saves you a lot of headaches.