It is important to know how to block access to files in Windows Server IIS, for example to prevent or stop spam mails from being sent. In this post I show you three methods to block access to a PHP file called "sendmail.php".
Suppose one of the websites you host on your Windows Server IIS webserver sends out spam, and you notice a X-PHP-Originating-Script header having sendmail.php in it as the responsible script. Here are three ways you can block access to that particular script.
Method 1: Block POST requests using a URL Rewrite Module rewrite rule
A quick way to stop the spam sending abuse is by blocking POST requests on a mail script or URL
<rule name="Block contact form spam" stopProcessing="true">
<match url="(.*)" ignoreCase="true" />
<conditions logicalGrouping="MatchAll">
<add input="{URL}" pattern="/sendmail.php" ignoreCase="true" negate="false" />
<add input="{REQUEST_METHOD}" pattern="POST" ignoreCase="true" negate="false" />
</conditions>
<action type="CustomResponse" statusCode="403" statusReason="Forbidden" statusDescription="Forbidden" />
</rule>
This IIS URL Rewrite Module rewrite rule is validated for every request, and when the condition matches TRUE, the request is blocked and a 403 Forbidden status code is send. Because the condition uses a MatchAll logicalGrouping, both input values ({URL} and {REQUEST_METHOD}) need to match, otherwise the rule is not evaluated as true.
Method 2: Block access to the file completely using a URL Rewrite Module rewrite rule
Another method is to completely block access to the file. In this scenario, the requested URL is evaluated, and if it matches sendmail.php, the request is blocked. Again, a custom 403 statuscode is send to the browser.
<rule name="Block sendmail.php" stopProcessing="true">
<match url="^sendmail\.php$" ignoreCase="false" />
<action type="CustomResponse" statusCode="403" statusReason="Forbidden" statusDescription="Forbidden" />
</rule>
- Deny vulnerable WordPress plugins using Windows Server File Server Resource Manager's File Screens
- Disallow direct access to PHP files in wp-content/uploads/
- IIS URL Rewrite "Rewrite Module error: Expression contains a repeat expression"
Method 3: IIS Request Filtering URL Deny Sequence
Use IIS Request Filtering feature to configure filtering rules. The IIS module RequestFilteringModule is loaded and executed prior to URL Rewrite Module. Using this module blocks access to the sendmail.php at an earlier stage and thus faster than using a URL Rewrite Module rewrite rule.
<security>
<requestFiltering>
<denyUrlSequences>
<add sequence="sendmail.php" />
</denyUrlSequences>
</requestFiltering>
</security>
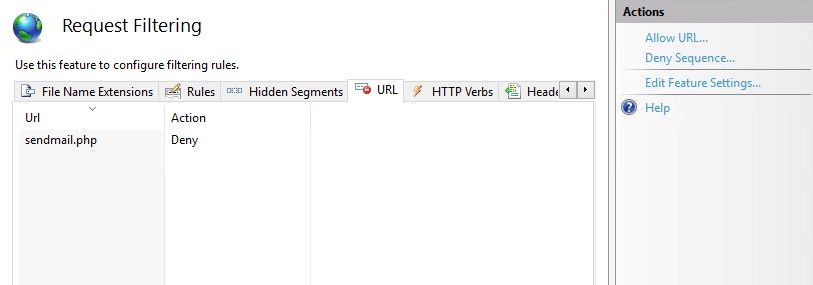
Please note that a Request Filtering rule sends out the following to the browser:
HTTP Error 404.5 - Not Found
The request filtering module is configured to deny the URL sequence.
This might give an attacker a clue he's blocked.
Conclusion blocking spam scripts like sendmail.php in IIS
As you can see, it's fairly easy and straightforward to block access to a particular PHP spam script on your Windows Server IIS webserver. Substitute "sendmail.php" with the script name in your scenario, and put the web.config file in the website physical path directory.